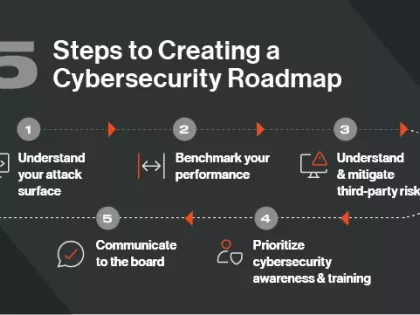
Budget cuts, growing vendor ecosystems, yet the stakes skyrocket. It’s a familiar script. But what if you could flip the script? These 5 strategies will help.

Bitsight and Diligent explore how boards are dealing with increasing cyber risk and whether there's a link between cybersecurity and financial performance.

Budget cuts, growing vendor ecosystems, yet the stakes skyrocket. It’s a familiar script. But what if you could flip the script? These 5 strategies will help.


_.pnge2fc.webp?itok=y2cnTjgy)


